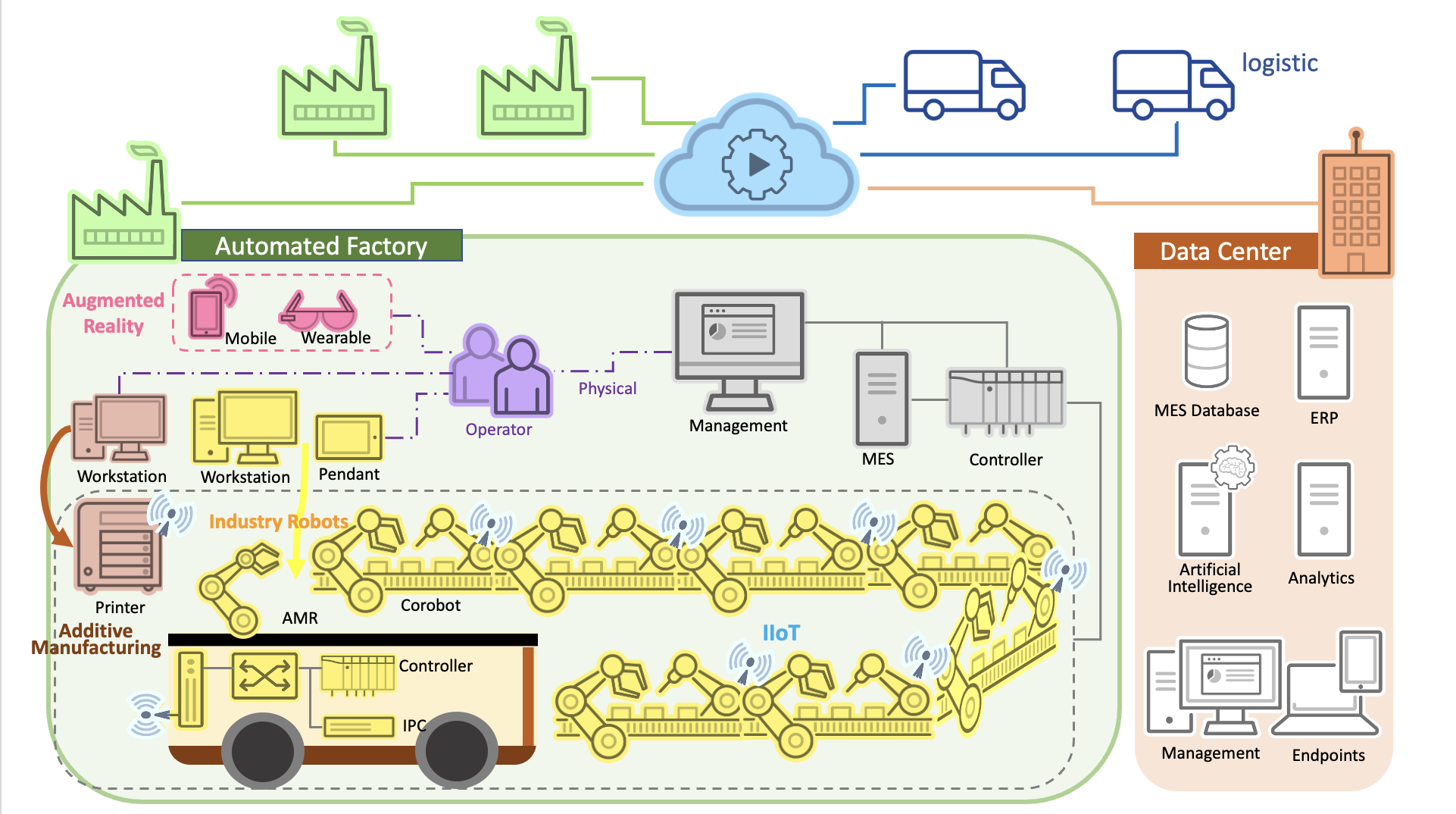
Automation in Production: A Background
The impacts of quarantine during the pandemic were hugely disruptive to the labor market and resulted in global labor shortages in the manufacturing industry. Meanwhile, geopolitics in conflict, including the U.S.-China trade war and the Russia-Ukraine war, have triggered a crisis in supply chain operations. Driven by the above external environmental factors, enterprises are accelerating the adoption of digital technology in order to evolve in a way that ensures operational resilience. According to Trend Force research in August 2021, the global smart manufacturing market size 2021 is US$305 billion; moreover, it is expected to grow to US$450 billion in 2025 with a 10.5% CAGR.
Automated Production: 4 Trends Impacting the Modern Factory
No matter who they are – automotive, aerospace, defense, oil, natural gas, or machinery equipment manufacturers – they are all rapidly starting up their smart manufacturing plans [1]. The global automated factory trends include the following [2][3][4]:
1. Industrial Internet of Things
To improve operational efficiency and reduce operating costs in the manufacturing industry, one of the trends in smart manufacturing is to deploy Industrial Internet of Things (IIoT) technologies to collect and analyze real-time data from the production shop floor and to adjust the process to optimize the workflow automatically. The IIoT refers to when traditional industrial control systems (ICSs) are connected to the Internet, which involves connecting machinery equipment and control systems to the network. For example, the blue icon in Figure 1 shows that heavy machinery is connected to the network through wireless technology. On the one hand, IIoT allows individual machinery equipment to provide real-time status data or operational results. On the other hand, if the data is further integrated into the factory information system or cloud systems such as Enterprise Resource Planning (ERP) or Manufacturing Execution System (MES), the data can be analyzed to and used to the benefit of tracking inventory, managing production quality, or controlling the manufacturing site. Furthermore, leveraging a vast amount of historical data can help manufacturers find ways to save costs. For example, when the sales department of an enterprise sends an ERP work order in the cloud to the MES of the factory, the work order information can be transmitted to the connected machinery equipment through the network so that the factory can successfully implement automation in the production process. In addition, due to the IIoT technology, the individual machinery equipment can provide the performance and operation status real-time so that enterprises can quickly check the manufacturing progress and quality. This allows them to then adjust the machinery in real-time if production conditions are changed.
2. Autonomous Mobile Robots and Collaborative Robots
Industrial robots are used in many large-scale manufacturing factories to assist humans in performing physical operations because of their efficiency, accuracy, and ability to operate in dangerous environments, which can significantly reduce the need for a labor force (please refer to Figure 1, where the industrial robots are marked with yellow). By using the pre-written program on the engineering computer, the engineer can upload the program to the robot according to the network services provided by the industrial robot, such as FTP, Web, or other communication protocols, so that the robot can automatically perform production operations. In addition, most robots provide Pendant to allow engineering personnel to perform functions on the shop floor. However, with the application of IIoT technology, industrial robots directly interact with the cloud more frequently. For example, a typical AMR (Autonomous Mobile Robot) consists of an industrial computer that runs the robot operating system, controller, and connectivity module. Furthermore, connectivity allows the robot to interact with other equipment in the factory using a wired or wireless network to upload real-time information to the cloud to provide more diverse applications, allowing enterprise supervisors to make optimal production strategies.
3. Augmented Reality
Due to workforce shortages, it is increasingly difficult for engineers to manage many different pieces of equipment simultaneously in a rapidly changing manufacturing environment. Therefore, wearable, or handheld, devices that can receive mechanical information and display additional visual information have become one of the trends in automated factories (please refer to Figure 1, where the wearable and handheld AR devices are marked with red). For example, a new employee who is not yet familiar with the business operation can optimize the workflow efficiency of the factory through augmented information displayed on the handheld device and follow the steps guided by the connected machinery. In addition, the augmented information can also display the immediate status of the machinery to assist engineers in the early detection of machinery issues that may impact production and reduce the risk of operational interruption. Engineers can also quickly access plan or analysis information recorded in the cloud by AR devices to assist in more operational decisions more quickly.
4. Additive Manufacturing (AM)
With the COVID-19 pandemic and its resulting economic impact on global supply chains across every major industry, many factories have suffered from the widespread delays and shortages in product components that brought entire operations to a standstill. The Biden Administration partnered with several leading US companies to launch AM Forward in May 2022. The primary purpose of AM Forward is to build more resilient and innovative supply chains by investing in small and medium-sized companies that develop AM technology [5]. AM technology is a computer-controlled process of creating a three-dimensional (3D) object by depositing materials and building it one layer at a time. It differs from traditional manufacturing, in which an object is created by cutting away at a solid block of material. In addition to speeding up production, AM technology can also save on a lot of material costs (refer to Figure 1, where the composition of AM technology is marked with brown). The actual cases of introducing the AM technology include the following: Medical device companies use AM technology to manufacture products with “porous internal structures” that cannot be achieved with traditional manufacturing processes. Another case is that the US Air Force uses AM technology to “print” the metal components that the equipment needs to replace, rather than relying on expensive inventory or components that have taken many years to acquire. According to our observations, AM technology is also one of the trends of manufacturing transformation.
Generally, the manufacturing process of an automated factory is highly digitalized, enabling the factory to use the data collected from the factory environment by the wired or wireless network so that the factory can respond more autonomously and flexibly to the changes inside and perimeter.
However, in order to correctly use and process a large amount of data, the IT and OT networks of enterprises have more interaction and integration today, which not only indirectly makes IT more vulnerable to being attacked but even increases the opportunity for adversaries to infiltrate the OT environment due to IT breaches. With the convergence of IT and OT, attackers have more entry points to try to break into the factory network. For example, machinery that initially installed a legacy operating system should be deployed in an isolated network. However, driven by intelligent manufacturing, that vulnerable machinery began to connect machinery to external networks. If the automated factory does not have a cybersecurity protection plan in place, adversaries have the opportunity to use operating system vulnerabilities to execute attacks against these connected devices, thereby affecting the regular operation of the factory.
Figure 1: Automated Factory Overview
Threats Faced by the Automated Factory
A survey report published by Trend Micro in 2021 pointed out that 61% of manufacturers have experienced cybersecurity incidents in their automated factories. Most incidents have caused system downtime, and 59% of manufacturers cannot find suitable cybersecurity solutions [6]. Besides, the system components or processes used in automated factories vary greatly due to the range of different purposes each manufacturer is fulfilling. As a result, few cybersecurity standards on the market are universally applicable for each enterprise. However, TXOne Networks analyzes the global trend of automated factories. We not only identify the following potential threats but also propose an adaptive cybersecurity solution for ICS shop floor protection to ensure the resilience of automated factories.
- Highly digitized factories connect a large number of machines to the network, allowing Initial Access attack techniques to appear in the factory environment
To improve manufacturing efficiency, factories can gradually adopt IIoT technology to connect the factory’s heavy machinery and systems to the network. At that point, they can collect and share a large amount of data across OT and IT platforms to acquire the benefits of predictive process adjustment by advanced analysis. The protocols commonly used in IIoT technology include MQTT, AMQP, and CoAP [7].
However, using these protocols without suitable cybersecurity configurations or protection will provide attackers with more vectors to execute initial attacks on these connected devices. Taking MQTT as an example, since this protocol is based on the principle of publishing messages and subscribing to topics, subscribers will not be able to know who is publishing messages. Thus, if an attacker connects to a server and publishes a message on existing topics, they can easily tamper with or overwrite the information, causing the factory equipment to execute unsafe behavior [8][9]. In addition, MES, SCADA, PLC, and sensors originally in the OT environment are connected to the external network in response to digitalization, thereby exposing industrial communication protocols with weak security capabilities, such as PROFINET, PROFIBUS, Ethernet/IP and Modbus and so on, to high levels of risk.
Furthermore, highly digitalized automated factories will also use a large number of wireless technologies. For example, machinery can transmit real-time manufacturing information to other machinery through RFID or NFC technology without contact so that other machinery can adjust accordingly and automatically. On the other hand, endpoint devices use WirelessHART or BLE to upload endpoint information to the cloud via a network gateway for enterprise data analysis and management [10]. It makes wireless network vulnerabilities vectors for the initial attacks of attackers. Many studies have found that these wireless network protocols are potentially vulnerable to denial of service, hijacking, or tampering [11][12][13][14]. In addition to having network defenses to limit trusted data sources, it is also necessary to have a visualization solution to manage the server. By learning the trusted behaviors of each device when attacked by attackers and early detection of attacked equipment, the most important thing is to prevent attackers from carrying out further attacks on the factory through the industrial communication protocols supported by the equipment. Network defense solutions can learn the trusted behavior of each piece of equipment.
- The development environment of industrial robots may be introduced with malware that enables highly privileged workstations to execute malicious behaviors
Industrial robots are used in many large-scale manufacturing activities due to their advantages of execution efficiency, accuracy, and ability to work in hazardous environments and significantly increase the production speed of factories. Industrial robots are already common in car manufacturing, food assembly, and the public sector that provides critical services. General industrial robots consist of a controller, robot, and workpiece. Engineers will control the industrial robot through workstations or Pendants. For safety reasons, robots sometimes use Cage to prevent engineers from approaching the robot in range of the robotic arm operating.
In addition, engineers can also download the development environment of the industrial robot to the workstation according to their brand (for example, Off-Line Programming (OLP). The robot can then automatically execute the work according to the script written in advance. To enable engineers to code programs quickly, some industrial robot suppliers will provide public services similar to app stores, and engineers can upload or download related extension kits according to their needs. If the supplier does not strictly inspect the uploaded content, the engineer may unintentionally download the malicious extension kits to the factory workstation and execute them, thereby posing a significant threat to the factory network [15].
Moreover, some industrial robots do not authenticate the access control by default. Under the trend of IIoT application, if an automated factory heedlessly exposes industrial equipment to the public network, attackers can directly exploit the vulnerable network protocol such as FTP, Web API, PROFINET, PROFIBUS, Ethernet/IP, and Modbus [16]. In some cases, public downloadable OLP software can modify controller parameters, production logic, or robot status, resulting in tampering with factory production outcomes [17].
- Keeping Augmented Reality devices improperly may allow the theft of confidential factory data and even the destruction of cloud data
Wearable or handheld devices with AR technology can enhance the interaction between engineers and machines. In addition to providing engineers with visualized machine operation processes or status, it can also access cloud data for real-time analysis and decision-making. An automated factory is similar to most OT environments. When equipment needs maintenance, equipment suppliers are often required to enter the factory area for processing, which makes the factory environment not wholly isolated. Suppose the AR device is not adequately protected by physical security. In that case, anyone’s AR device may be stolen by an adversary who sneaks into the factory to steal the AR device and obtain confidential information about the factory. Information such as, for example, new production processes in pharmaceutical factories or product formulations in food factories[18][19]. Even if it is an AR device for engineers, adversaries can use it to access the enterprise cloud data, thereby expanding the impact in allover factories. Usually, these people’s devices are considered trusted sources [20].
- Due to the working principle of AM equipment, when the configuration file is tampered with by an attacker, the equipment may burn and cause a large-scale disaster in the factory
Since global supply chains have suffered from widespread delays and shortages in product components. Many manufacturing plants are gradually introducing AM technology to enhance component manufacturing capabilities to shorten production’s life cycle. In the trend of 2022, the use of AM technology will continue to grow in automated factories related to the aerospace, automotive or medical industries [21][22]. In the past, SANS researchers had found that thousands of insecure AM devices are exposed to the public network and can control the devices without authorization. However, when most AM devices used unencrypted files (G-code format) to control the way of printing, attackers had the opportunity to steal confidential information about products being developed or tested in factories [23]. Besides, some AM devices will also open web services for firmware updates. When an attacker connects to the device or executes ARP Spoofing on the same network segment, the AM device can also install malicious firmware, making the device persistent. Excessive heating caused large-scale disasters in factories [24].
Learn more about the threat terrain to the modern factory in our comprehensive guide.
How to Mitigate Potential Threats to Automated Factories
Due to different industrial purposes, system components or processes adopted by automated factories are highly divergent. Only a few cybersecurity standards on the market are universally applicable to each enterprise. In addition, emerging technologies such as IIoT, AMRs, cobots, AR, and AM are applied to global automated factories, which require factories to manage a large number of connected devices simultaneously. TXOne Networks offers cybersecurity solutions that ensure the operation reliability and digital safety of ICS and OT environments through the OT zero trust methodology.
- Inspect: Due to the rise of Industrial IoT technology, many factories’ machines or systems are connected to the Internet for real-time data collection and sharing. Therefore, when an industrial robot or additive manufacturing equipment specifically designed for scripting is attacked by malware and brought into a factory’s internal network by an employee, the device may distribute the malware to each factory. Thus, we must conduct a security inspection before new equipment enters the shopfloor to prevent insiders from intentionally or unintentionally bringing malware into the factory environment.
- Lock Down: Most of the equipment in an automated factory has fixed objects and contents. For example, engineering computers that operate exclusively on industrial robots use specific network protocols to operate robots rather than accessing PLC or MES information. We can stop malicious behavior and misoperation in one fell swoop with OT protocol command-specific allow lists at the network level. Even if successfully connected to a factory device using a trusted source, with the least privilege to execute operations, only trusted applications or websites are allowed to run on the device at the application level. So, even if an engineer unintentionally downloads a malicious extension kit on a factory workstation, the software cannot run normally.
- Segment: Many different automated production lines are operating in a large factory at the same time. Network segmentation arranges enterprise assets into isolated groups based on their purpose, sharply limiting options for attack, and those attacks can be restricted to a specific area so that the attack’s damage will not continue to spread.
- Reinforce: Similar to most industrial control systems, if the operation of the equipment in the automated factory is interrupted, it will bring significant financial losses to the enterprise. Thus, we recommend using virtual patching to block loopholes on the MES and shield vulnerabilities of legacy or unpatchable systems protecting sensitive critical assets. When the production line is in the annual maintenance period, the loopholes can be patched so that the automated factory can continue to operate.
References:
[1] P.K Tseng, “Global Smart Manufacturing Revenue for 2021 Expected to Reach US305 Billion Thanks to Increased Digital Transformation and WFH Demand, Says TrendForce”, TrendForce, Aug 18 2021, Accessed Aug 5 2022
[2] Emergen Research, “Top 10 Globally Leading Companies Offering Next-Generation Smart Factory Solutions”, Emergen Research, Apr 7 2022, Accessed Aug 5 2022
[3] Gloria, “5 Smart Manufacturing Trends to Boost Productivity in 2022”, SwipeGuide, May 11 2022, Accessed Aug 5 2022
[4] STMicroelectronics, “Semiconductors are a Key Enabler for Smart Industry”, STMicroelectronics, Accessed Aug 5 2022
[5] The White House Blog, “Using Additive Manufacturing to Improve Supply Chain Resilience and Bolster Small and Mid-Size Firms”, The White House, May 9 2022, Accessed Aug 9 2022
[6] Trend Micro, “Smart Factory Cyber Attacks Knock Out Production for Days”, Trend Micro, Mar 29 2021, Accessed Aug 5 2022
[7] Moxa, “Make Your OT, IT, IIoT Protocol Interoperability Easier for Industry 4.0”, Moxa, Accessed Aug 9 2022
[8] HiveMQ White Paper, “Modernizing the Smart Manufacturing Industry with MQTT”, HiveMQ, Accessed Aug 5 2022
[9] TXOne Networks Blog, “MQTT Series #2: Potential Risks of Exposed MQTT Brokers”, TXOne Networks, Jan 2 2020, Accessed Aug 5 2022
[10] Emerson Electric White Paper, “Industrial IoT Devices: WirelessHART and 5G”, Emerson Electric, May 2020, Accessed Aug 5 2022
[11] ICS-CERT Advisories, “Emerson WirelessHART Gateway”, CISA, Oct 19 2021, Accessed Aug 5 2022
[12] Santiago Figueroa Lorenzo, Javier Añorga Benito, Pablo García Cardarelli, Jon Alberdi Garaia, Saioa Arrizabalaga Juaristi, “A Comprehensive Review of RFID and Bluetooth Security: Practical Analysis”, MDPI, Jan 24 2019, Accessed Aug 5 2022
[13] Suzanne Smiley, “7 Types of Security Attacks on RFID Systems”, Atlas RFID Store, Jun 14 2016, Accessed Aug 5 2022
[14] Shahid Raza, “Secure Communication in WirelessHART and its Integration with Legacy HART”, Swedish Institute of Computer Science, Jan 13 2010, Accessed Aug 5 2022
[15] Federico Maggi, Marco Balduzzi, Rainer Vosseler, Martin Rösler, Walter Quadrini, Giacomo Tavola, Marcello Pogliani, Davide Quarta, Stefano Zanero, “Smart Factory Security: A Case Study on a Modular Smart Manufacturing System”, ScienceDirect, 2021, Accessed Aug 5 2022
[16] Robotiq, “Industrial Robot Communication Protocols”, Robotiq, Jun 2013, Accessed Aug 9 2022
[17] Trend Micro Security News, “Rogue Robots”, Trend Micro, May 3 2017, Accessed Aug 5 2022
[18] Naveen Joshi, ”4 Applications of Augmented Reality in Pharmaceuticals”, BBN Times, Apr 27 2022, Accessed Aug 9 2022
[19] Emily Vencat, “How Augmented Reality Will Shape the Food Industry”, YouBar, Mar 3 2020, Accessed Aug 9 2022
[20] Ramsey Hajj, Sean Peasley, Jason Hunt, Heather Ashton Manolian, David Beckof, “Cyber Security for Smart Factories”, Deloitte, 2020, Accessed Aug 5 2022
[21] YOAV ZEIF, “Four 3D Printing Trends to Look for in 2022”, Fast Company, Mar 11 2022, Accessed Aug 5 2022
[22] MICHAEL PETCH, “2022 Trends in 3D Printing, Forecasts from ADditive Manufacturing Experts and Leaders”, 3D Printing Industry, Jan 17 2022, Accessed Aug 5 2022
[23] Xavier Mertens, “3D Printers in the Wild, What Can Go Wrong?”, SANS Institute, Aug 30 2018, Accessed Aug 5 2022
[24] Dan McInerney, “With IoT, Common Devices Pose New Threats”, Coalfire, Accessed Aug 5 2022