CBTC Systems: a Background
Communication-Based Train Control (CBTC) is a state-of-the-art railway signaling system that leverages electronic, communication, and automatic control technologies to provide enhanced precision in train operation control. With traditional fixed signal systems, a series of fixed signal devices installed along railway tracks is required to guide train movements. In CBTC system architecture, however, wireless communication technology is employed to transmit train data, including location and speed, to the train control center. This allows for more accurate train operation control, encompassing automatic control of acceleration, deceleration, stopping, and turning.
Due to CBTC’s real-time monitoring of train positions and speeds, it can precisely control train scheduling, enabling trains to operate at higher speeds. This not only improves transportation efficiency but also mitigates the risk of train collisions.
Internationally, numerous cities have adopted CBTC to manage subway, light rail, and high-speed railway transportation systems. Some notable applications include the ATC (Automatic Train Control) in the New York City Subway, the ASFA (Anuncio de Señales y Frenado Automático) on Spain’s AVE high-speed railway, and the SELTrac on France’s Lille light rail.
Figure 1. Communication-Based Train Control Architecture
As shown in Figure 1, the application of CBTC involves installing transponders (depicted in brown) at fixed intervals along the train tracks. Whenever a train passes a transponder, the on-board receiver can wirelessly obtain location information from the transponder. In conjunction with the train’s speed sensor (depicted in green), the train can determine its precise location based on the last encountered transponder and speed information, automatically calculated by the controller.
Next, the train wirelessly exchanges data with the wayside system. At this point, the wayside controller calculates movement permissions and restrictions for each train based on the provided information. Lastly, the wayside system transmits the data to the Control Center. Within the Control Center, operators can monitor the complete track status and train positions using the SCADA system, and if necessary, adjust train schedules or issue control commands. Railway SCADA is illustrated in Figure 2.
Figure 2. Schematic Picture of Railway SCADA
Within CBTC system architecture, the Data Communication System (DCS) – responsible for collecting and transmitting information on train position, speed, direction, etc. and facilitating data exchange between various CBTC subsystems – is primarily composed of backbone networks and wireless networks. The backbone network serves as the transmission channel between ground-based railway equipment, such as switches that guide trains onto different tracks, signals that provide instructions to drivers or dispatchers, and track circuits that detect obstacles on the tracks. Meanwhile, wireless networks enable data exchange between onboard and wayside equipment. For example, SELTrac utilizes WLAN technology based on IEEE 802.11 for high bandwidth and real-time advantages.
Although there have been no historical cases of direct network attacks on CBTC causing train accidents, considering CBTC manages many critical modules–such as Automatic Train Protection (ATP), which automatically applies brakes when trains exceed the specified speed, and Automatic Train Operation (ATO), which adjusts train speed and glide control–threat organizations with specific objectives may still target CBTC in the future.
Cyber Threats Posed by CBTC Wireless Communications
1. Vulnerabilities in WLAN wireless transmission present the possibility of CBTC communication disruption
Since trains are typically open spaces, passengers can bring their laptops and attempt network attacks on wireless transmissions from their seats without any hindrance. For instance, CBTC that adopts WLAN technology based on IEEE 802.11 has inherent cybersecurity flaws in its standard:
A. Management frame attacks:
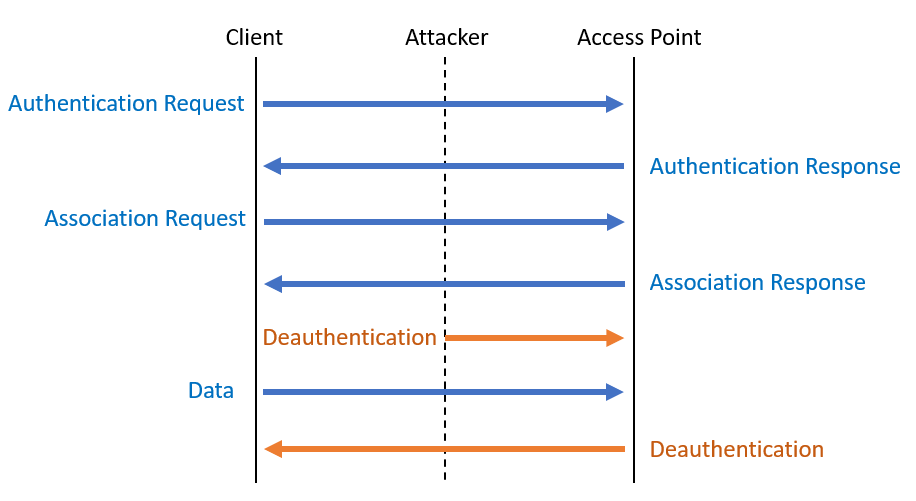
This mainly occurs when many management frames are not authenticated, allowing attackers to send forged MAC address management frames, affecting the connections of other clients. This is due to the protocol mechanism (as shown in Figure 3), where clients must authenticate their identity to the AP. Attackers can send a Deauthentication frame with the victim’s MAC address to the AP at any time, forcing the victim to exit the authenticated state and reject all further packets until they re-establish authentication with the AP. Attackers can repeatedly carry out this attack, indefinitely preventing the victim from sending or receiving data, causing the CBTC subsystems to fail in normal communication.
Figure 3. Deauthentication Frame
B. Brute-force password cracking:
During the 4-way handshake between the client and the Access Point (AP), many parameters are transmitted in plaintext, including MAC addresses (devices must know each other’s MAC addresses to connect), BSSID, and MIC (used to verify packet integrity). The WLAN password and these parameters can be obtained through a fixed algorithm. Therefore, an attacker can use a dictionary file combined with parameters from the packet to calculate the MIC and compare it with the AP’s MIC. If the two match, the correct password has been found. In this scenario, the attacker only needs a wireless network card that supports Monitor Mode and can use the airmon-ng tool to monitor handshake packets on the train. After saving the packets, the attacker can use a pre-prepared dictionary file to find the target password through offline brute-force cracking. Figure 4 shows the execution screen of airmon-ng performing a dictionary file attack.
Figure 4. Executing a Dictionary Attack Using Airmon-ng
C. 802.11i attack:
To protect wireless networks, 802.11i has been designed to prevent continuous attacks on the Access Point (AP). Its measures include closing the session for 1 minute if the WLAN AP receives more than one invalid MIC checksum. A new session key must be generated for reconnection, limiting attackers to only one attack attempt per minute across the entire network. However, this also allows attackers the opportunity to temporarily suspend wireless services by repeatedly sending forged MIC checksums.
Executing such attacks is relatively difficult, as the attacker must obtain a valid Frame during data transmission and not only prevent the Frame from reaching its destination but also trigger an invalid MIC checksum. Nevertheless, threat organizations targeting CBTC systems may still attempt this method to disrupt train data transmission.
2. Transponder interference attacks prevent trains from accurately receiving location information
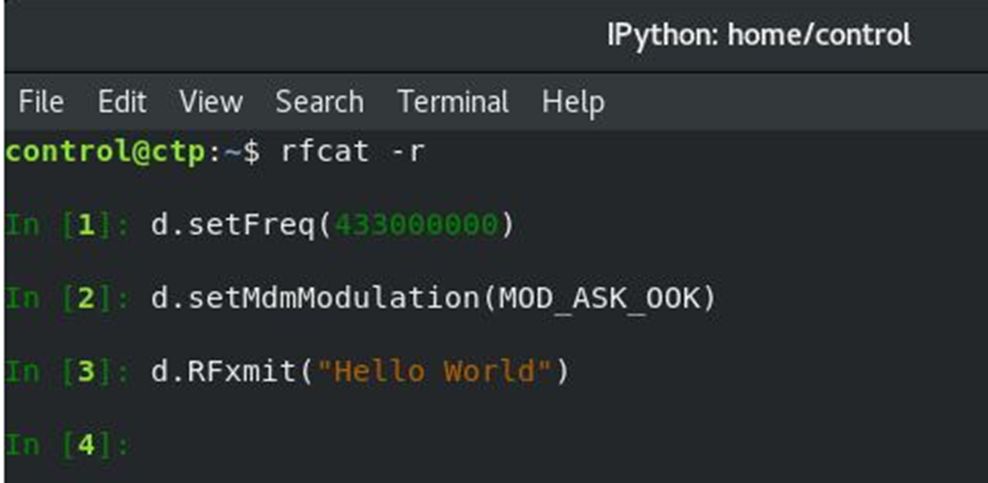
As mentioned earlier, Transponders are installed at fixed distances along the train tracks to provide location information to the train’s Receiver via wireless signals. For example, the European Train Control System (ETCS) uses a frequency of 4.234 MHz ± 5 kHz, modulated using Frequency Shift Keying (FSK). Based on experiments, we know that an attacker can use an RTL-SDR tool on a laptop and transmit the specified frequency and modulation method using the rfcat command, as shown in Figure 5. Additionally, in the study, researchers successfully recreated an interference attack in the FSK modulation using real railway equipment and a Transponder in a laboratory environment (see Figure 6). As a result, the ETCS system was temporarily suspended, and the train was forced to stop.
Figure 5. Transmitting Specified Frequency and Modulation Method Using rfcat Command
Figure 6. Reproducing Interference Attack in FSK Modulation
3. Exposed network equipment provides attackers with opportunities for physical attacks
CBTC utilizes a large number of communication devices as data exchange nodes, and these routers and other devices scattered across the Wayside may be vulnerable to physical attacks, which could affect CBTC’s network communication. Although CBTC has redundant designs and relevant security mechanisms to ensure train operation safety, these mechanisms may reduce the efficiency of train operations when the system is under attack. In the event of a communication interruption, the safety mechanism will stop the train in an emergency, resulting in significant economic losses. In our past experience of disassembling router devices, we found that most circuit boards have debug interfaces (such as UART, JTAG, or GPIO), which often lack proper authentication mechanisms. This allows attackers to directly access routers using corresponding tools and open backdoor services, launching attacks on a large number of routers when the timing is right. Figure 7 shows our implementation of an attack on a router’s debug interface using an Attify badge.
Figure 7. Executing an Attack on a Router’s Debug Interface Using an Attify Badge
Moreover, CBTC suppliers install numerous maintenance and monitoring devices and enable hidden control interfaces for maintenance purposes, allowing maintenance teams to quickly access CBTC data. However, these interfaces often overlook network access restrictions, giving attackers the opportunity to identify and exploit these unprotected interfaces, ultimately jeopardizing train operation safety.
Conclusion
1. CBTC’s extensive use of wireless communication technology provides attackers with opportunities to execute interference attacks on the system
Although there have been no reported cases of attackers directly executing network attacks on CBTC, causing train accidents, older train systems may use outdated wireless communication technologies that are susceptible to sniffing, rogue AP, MITM, and DoS attacks (as mentioned earlier). While train safety mechanisms can prevent large-scale disasters, targeted threat organizations may still take advantage of these safety mechanisms to force trains to stop suddenly, causing massive disruptions to a country’s transportation system.
2. Interconnecting systems with different security levels in the railway industry provides attackers with opportunities to impact CBTC through lateral movement
Cyberattacks in the railway industry continue to emerge. Recent incidents include a ransomware attack on an Italian railway company’s IT system in March 2022, which led to a suspension of all train operations due to its inability to update passenger information. In October 2022, Denmark’s Supeo company was targeted by a cyberattack, causing all trains to come to a halt as drivers were unable to access critical information through their apps [7][8]. As more CBTC systems interconnect with systems of different security levels to utilize the full benefits of digitalization, (one of which is connecting to passenger information systems to provide real-time train location updates to station and onboard passengers), ensuring the legitimacy of data transmission becomes paramount. If not effectively addressed, threat organizations may have opportunities to penetrate CBTC systems continuously, causing even more severe impacts on the railway industry.
3. Due to security constraints, it is difficult to patch vulnerabilities in CBTC equipment, exposing the system to numerous known vulnerabilities
CBTC-related systems require lengthy and complex security audit processes. However, these systems widely use off-the-shelf software and operating systems, inevitably leading to known vulnerabilities. This allows attackers with access to the CBTC network to exploit these vulnerabilities, install malicious software on servers, and lay dormant, undetected. When the time is right, attackers can then remotely execute code to cause system crashes, forcing train personnel to switch trains to manual mode to prevent accidents.